- Created by Vladimir Stanković on 17 08, 2018
The main goals of this article are to (1) provide you with examples of Traffic Patterns and their usage and (2) to give you an idea on how to create your own Traffic Patterns. In this article only basic Traffic Patterns, that can be created with only IP address ranges and de-duplication filters, will be explained.
General workflow for creating new Traffic Pattern:
- Determine the traffic of interest;
- Determine which Traffic Pattern type to use (it will help you with populating Internal and External Network address ranges);
- Determine IP address ranges for Internal and External Networks;
- Determine which filter (if any) you should use to filter traffic further, if needed.
Basic Traffic Patterns
All Traffic Pattern
All Traffic Pattern gives the answer to "How my network is communicating to the rest of the world?". Here your company's IP address range is treated as Internal network, whereas all other (both belonging to your company and not) as External network.
By default, NetVizura provides All Traffic Pattern with predefined IPv4 address ranges (10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16). However, if your company uses different IP address range than predefined you need to change All Traffic Pattern. Since this is practically the traffic between your network and everything else you should select Custom type and update Internal IP addresses leaving External empty. In the end, you should use Exporter or Next Hop filtering to remove eventual duplicate flows, if needed.
- Edit All Traffic
- Select Custom as Traffic Pattern type
- IP Address ranges:
- Internal: if necessary, change your company network's IP range(s) and click Include
- External: leave empty
- Filters:
- Exporter or Next Hop: read more about Manual Deduplication
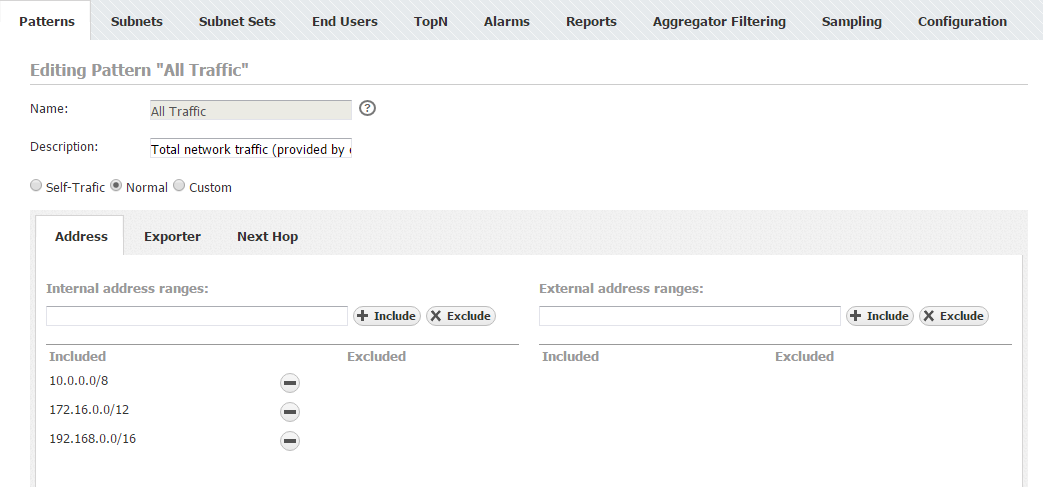
Internet Traffic Pattern
If you are interested in monitoring Internet traffic, first you need to prepare a specific Traffic Pattern for this purpose. Since this is practically the traffic between your network and outside world where External network is negation of Internal Network) you should select Normal type which will automatically populate part of the IP address ranges. Here your company's IP address range is treated as Internal, whereas all other networks as External. In the end, you should use Exporter or Next Hop filtering to remove eventual duplicate flows, if needed.
- Create Internet Traffic
- Select Normal (default) as Traffic Pattern type
- IP Address ranges:
- Internal: Add your company network's IP range(s) and click Include
- External: your company network's range is excluded automatically
- Filters:
- Exporter or Next Hop: read more about Manual Deduplication
- Exporter or Next Hop: read more about Manual Deduplication
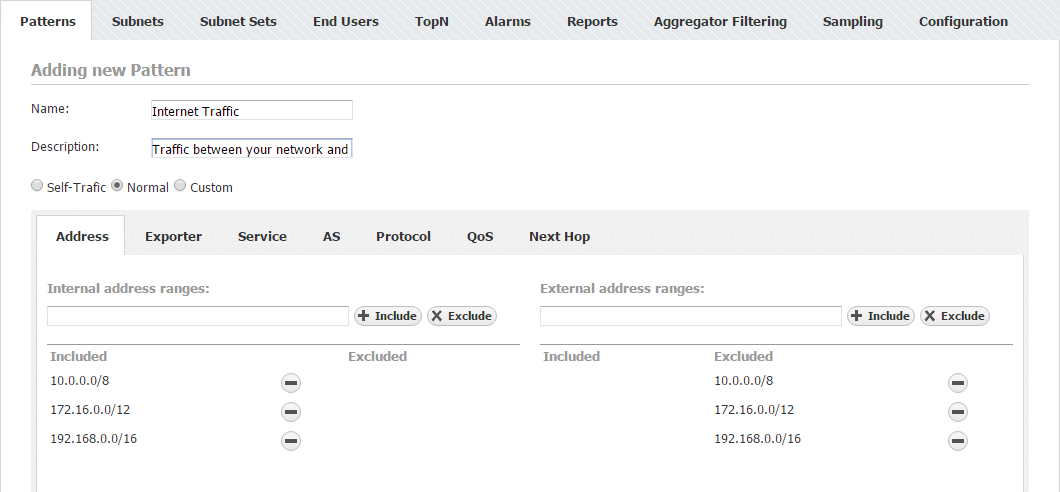
Data Center Traffic Pattern
Another example of most commonly used Traffic Pattern is Data Center Traffic.This traffic occurs between all your company and your data center, you should include you company's IP address range and exclude your data center's IP range in Internal Network, and include you data center's IP range in External network (here your data center is treated as "Outside" network). Since Internal Network (company network without Data center) and External Network (Data Center) IP ranges overlap you should use Custom type (turns off automatic IP address range population). Do not forget Exporter or Next Hop filtering to remove duplicate flows, if needed.
- Create Data Center Traffic
- Select Custom as Traffic Pattern type
- IP Address ranges:
- Internal: add your company network's range and click Include
- Internal: add your data center's range and click Exclude
- External: add your data center's range and click Include
- Filters:
- Exporter or Next Hop: read more about Manual Deduplication
- Exporter or Next Hop: read more about Manual Deduplication
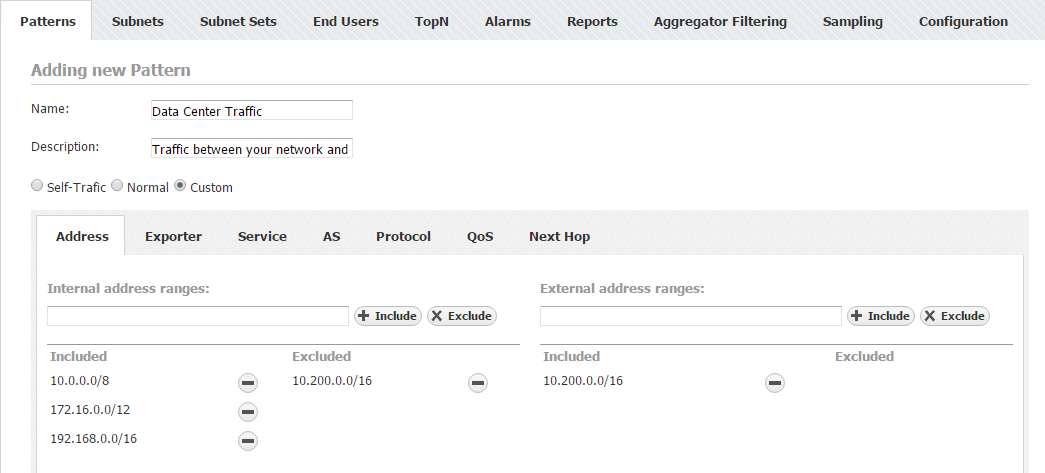
Advanced Traffic Patterns
This article uses filtering based on netflow parameters. For more information on how to add a specific filter, see chapter Traffic Pattern Settings and article Fine-tuning a Traffic Pattern.
Dropped Traffic Pattern
Dropped Traffic is the traffic that your network devices send to the Null interface. On Cisco routers, traffic is sent to the null interface if you have invalid routing (routing tables are not complete) or the traffic is blocked by access lists. So, this traffic can give you information on (1) routing problems and (2) on blocked traffic, which is potentially an attack or an attempt of unauthorized access to your network.
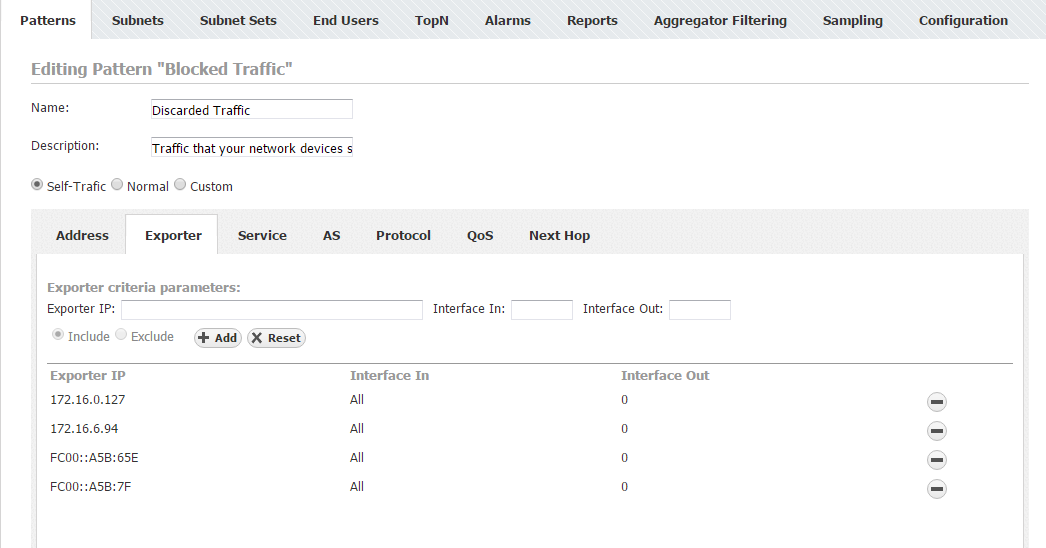
Let us see how to make a Traffic Pattern for this purpose. You are only interested in the traffic within your network, so you should create a Self-Traffic type. This being said, you should only set the Internal Network IP address range to your company network's whereas your company network's range will be automatically included in the External network IP address range (Self-Traffic). As for using filters, since you are interested in the dropped traffic (null interfaces), you need to use the Exporter filter. Furthermore, as you are interested in dropped traffic on all exporters, you need to include all exporters into the filter while setting the Out interface field to 0 (code for the null value).
- Select Self-Traffic (Traffic Pattern type)
- IP Address ranges:
- Internal: include your company network's range
- External: your company network's range is included automatically (Self-Traffic)
- Filters:
- Click on the Exporter:
- Add Exporter IP address and set Interface Out value to 0, click Include
It is necessary to repeat this step for each exporter that are sending netflow data to your NetFlow Analyzer.
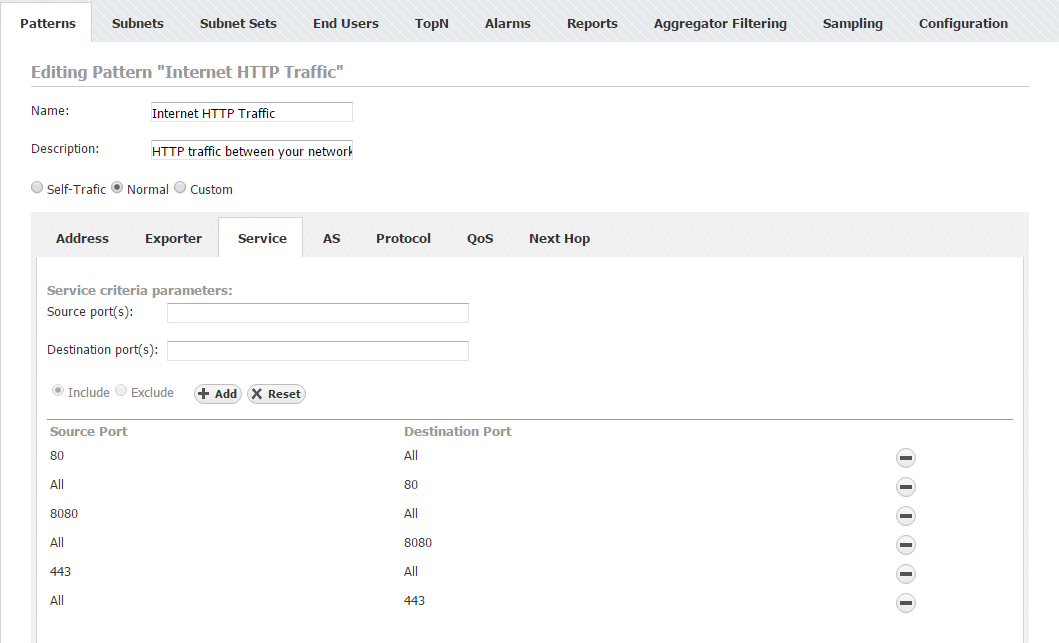
Internet HTTP Traffic Pattern
In some cases, you might want to take a detailed look at HTTP traffic. Since this traffic is between an outside network and your internal network, you should use the Normal Traffic Pattern type. You need cover the traffic between your whole internal network and any other network (Internet). This being said, you should set the Internal Network IP address range to your company network's range - the External network IP address range will be populated automatically (Normal Traffic). As for using the filters, since you are dealing with a web service which is recognized by its port(s), you need to use an Service filter and enter its Service number, HTTP (80) in this example.
- Select Normal (default Traffic Pattern type)
- IP Address ranges:
- Internal: include your company network's range
- External: your company network's range is excluded automatically
- Filters:
- Exporter or Next Hop: read more about Manual Deduplication
- Service:
- Include Source port(s) 80 / Destination port(s) empty (All)
- Include Source port(s): empty (All) / Destination port(s) 80
It is necessary to repeat this step for each port that is used for HTTP (eg. 8080, 443, etc.).
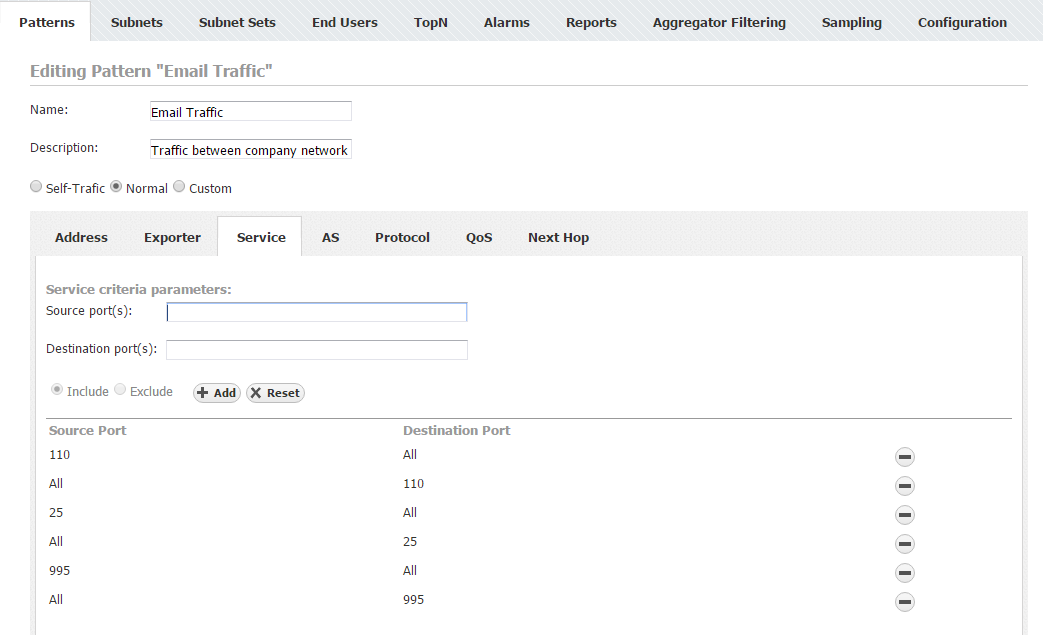
Email Traffic Pattern
Your can use NetFlow Analyzer for dedicated monitoring of your Email traffic. You should use the Custom Traffic Pattern type, since IP address ranges overlap. You need to cover the traffic between your whole internal network with mail servers. This being said, you should set the Internal Network IP address range to your company network's range, with exception of your mail server's IP, and set the External network IP address range as your mail server's IP (in this case your email server is treated as "Outside" network). As for using the filters, since you are interested in service which is recognized by its port(s), you need to use an Service filter and add Service number for the service, Email POP3 port (110) in this example.
- Select Custom (Traffic Pattern type)
- Address
- Internal: include your company network's range, and exclude you mail server's IP
- External: include you mail server's IP
- Filters:
- Exporter or Next Hop: read more about Manual Deduplication
- Service
- Include Source port(s): 110 / Destination: empty (All)
- Include Source port(s): empty (All) / Destination: 110
It is necessary to repeat this step for each port used for email traffic (eg. 25, 995, ...).
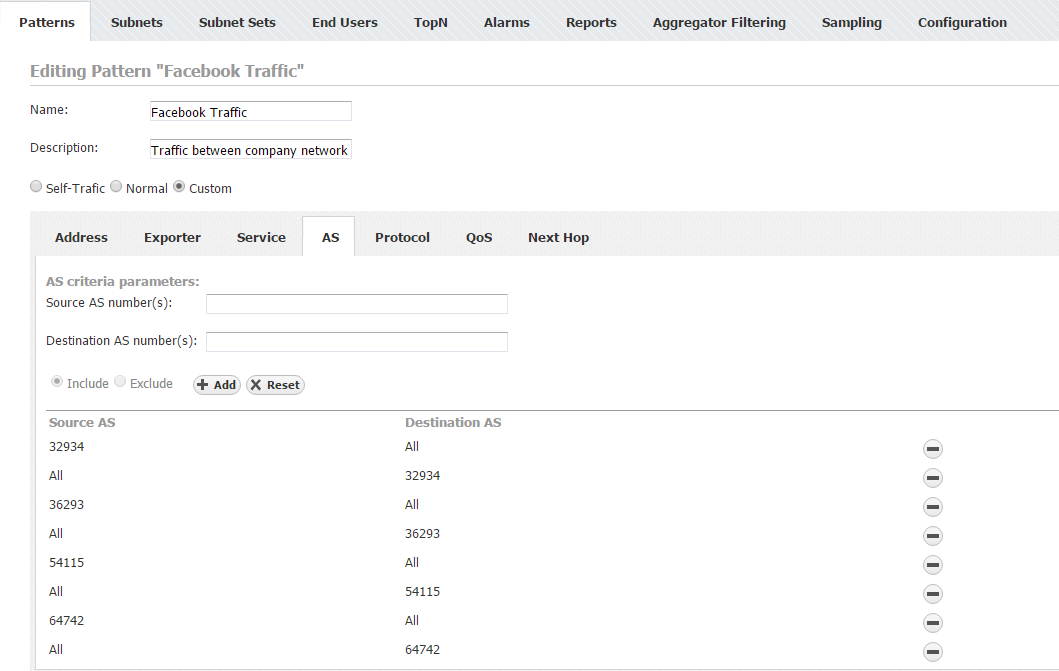
Facebook Traffic Pattern
You may want to measure the traffic between your network (or its part) and a specific web service such as Facebook. Since this traffic is between an outside network (Facebook) and your internal network, you should use the Normal Traffic Pattern type. You need to cover traffic between your whole internal network and any other network. This being said, you should set the Internal Network IP address range to your company network's range - the External network IP address range will be populated automatically (Normal Traffic). As for using the filters, since you are interested in a web service which is recognized by its AS, you need to use an AS filter and enter AS number for the service, in this example the ASN is Facebook's ASN (32934).
- Select Normal (default Traffic Pattern type)
- IP Address ranges:
- Internal: include your company network's range
- External:
- your company network's range is excluded automatically
- Filters:
- Exporter or Next Hop: read more about Manual Deduplication
- AS
- Include Source port(s): 32934 / Destination: empty (All)
- Include Source: empty (All) / Destination: 32934
It is necessary to repeat this step for each ASN used by Facebook (eg. 36293, 54115, 64742...).
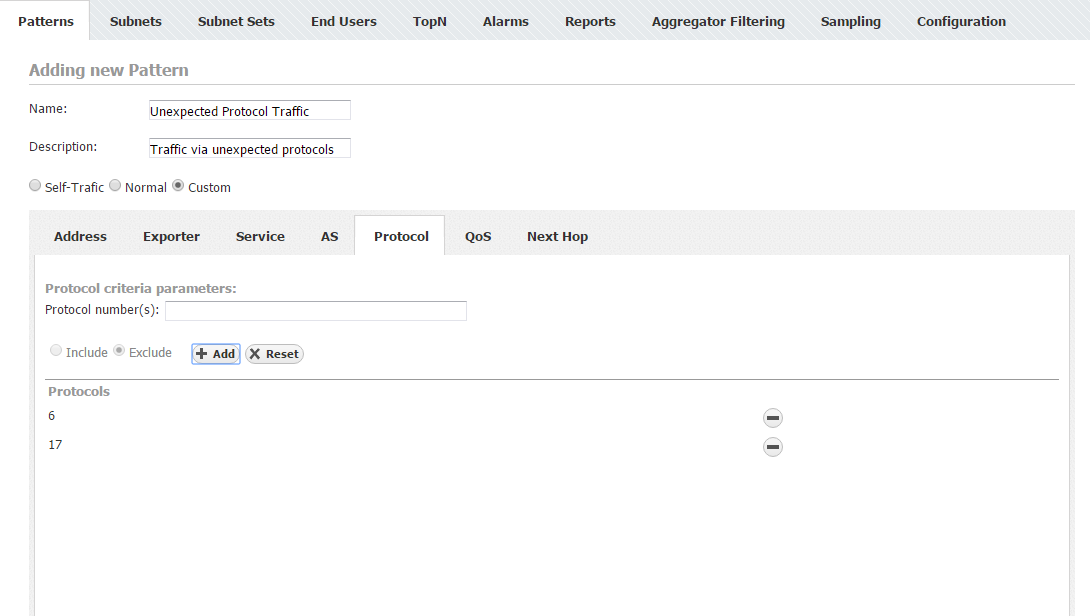
Unexpected Protocols Traffic Pattern
Some traffic important to you might be small in the terms of volume and, therefore, not easily spotted on charts and graphs, if so - create a separate Traffic Pattern for that traffic. One example of this is when you are interested in traffic made by protocols other then UDP and TCP. Since these two protocols usually take up to 99% of all traffic, it will be hard to spot any other protocol on graphs. Protocols other then TCP and UDP (we will call them unexpected protocols) might indicate a tunneling protocol or a potential attack.
Let us see how to make a Traffic Pattern for this purpose. You need to cover the traffic between your whole internal network and any other network - attacks are usually expected to come from the External Network to Internal Network (your internal network), but keep in mind that your own network security can be compromised and an attack might be launched from your network to some other network (both Internal and External network). You will do that by choosing Custom for the Traffic Pattern type. This being said, you should set the Internal network IP address range to your company's network range and leave the External network IP address range empty, since you want to cover all other networks. As for using the filters, since you are interested in protocols, you need to use the Protocol filter and enter service port numbers for TCP and UDP which are 6 and 17.
- Select Custom (Traffic Pattern type)
- IP Address ranges:
- Internal: include your company network's range
- External: leave empty
- Filters:
- Exporter or Next Hop: read more about Manual Deduplication
- Protocol
- Exclude Protocol number(s): 6
- Exclude Protocol number(s): 17
- No labels