- Created by Vladimir Stanković, last modified on 24 08, 2016
NetVizura is capable of detecting end user activity in the company network. End user traffic is identified by mapping IP address provided in syslog logon event and IP address provided in NetFlow data. Logon events could be generated by Domain Controllers or Work Stations relayed via Syslog server to NetVizura server. We use Windows Domain Controller in our example.
NetVizura comes with predefined matching rules for Snare Open Source Syslog agent:
In ![]() > Settings > NetFlow Settings > End Users there is already predefined logon rules for collecting logon events from Snare syslog agent. You can activate it by clicking Active at Status field. Double click on rule opens rule condition where you can change Source IP to more specific value to increase performance and check collection of logon events by clicking on Verify match.
> Settings > NetFlow Settings > End Users there is already predefined logon rules for collecting logon events from Snare syslog agent. You can activate it by clicking Active at Status field. Double click on rule opens rule condition where you can change Source IP to more specific value to increase performance and check collection of logon events by clicking on Verify match.
For detailed explanation on how to install and configure Snare Syslog agent see Installing and Configuring Syslog Agent for End User Traffic.
Example of correct match string from Snare
* MSWinEventLog * 4624 Microsoft-Windows-Security-Auditing * Success Audit * Logon Type: 3 * Account Name: <USERNAME> * Account Domain: <DOMAIN> * Source Network Address: <USER-IP> *
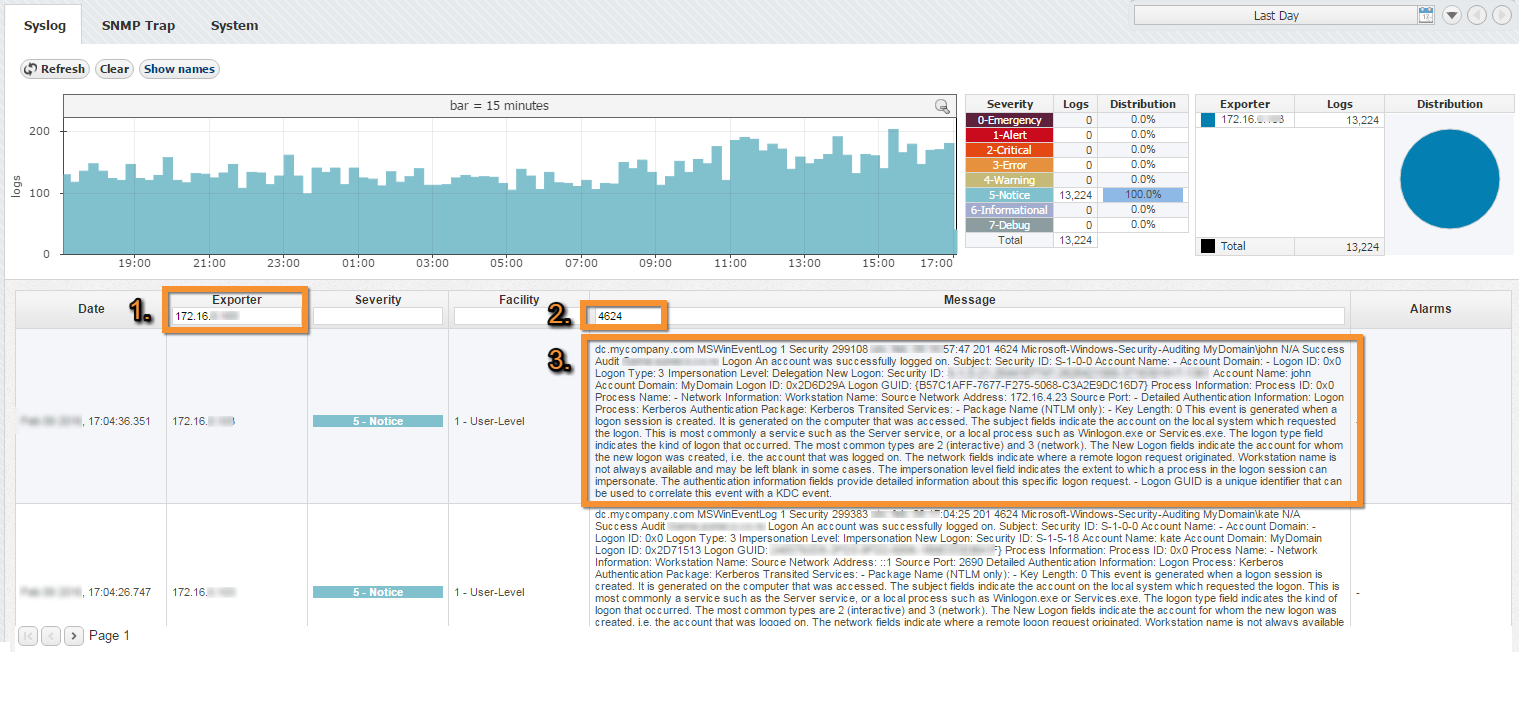
Step 1. Select appropriate message (logon event):
Navigate to Netvizura Eventlog module and choose Syslog tab. Identify syslog message with logon information. This log should contain:
IP address of domain controller that exports Syslogs - type IP address into Exporter text box and press Enter
- Windows code 4624 that designates successful logon event - type 4624 into Message filter text box and press Enter
- Select, copy and paste text message in some text editor (Wordpad or similar)
- Create appropriate Match string in text editor
Match String
Steps for creating correct match string :
- Find Account Name within the message and put <USERNAME> instead of real account name (please refer to picture below)
- Find Account Domain within the message and put <DOMAIN> instead of real account domain (please refer to picture below)
- Find Source Network Address within the message and put <USER-IP> instead of real IP address (please refer to picture below).
No need for this step in case of Work Station type of rule.
- Find additional information that can help in matching message more precisely like: MSWinEventLog, 4624 Microsoft-Windows-Security-Auditing, Success Audit, Logon Type: 3
- IMPORTANT: Delete any other text and put * as a wildcard instead of deleted text (refer to Example of correct match string)
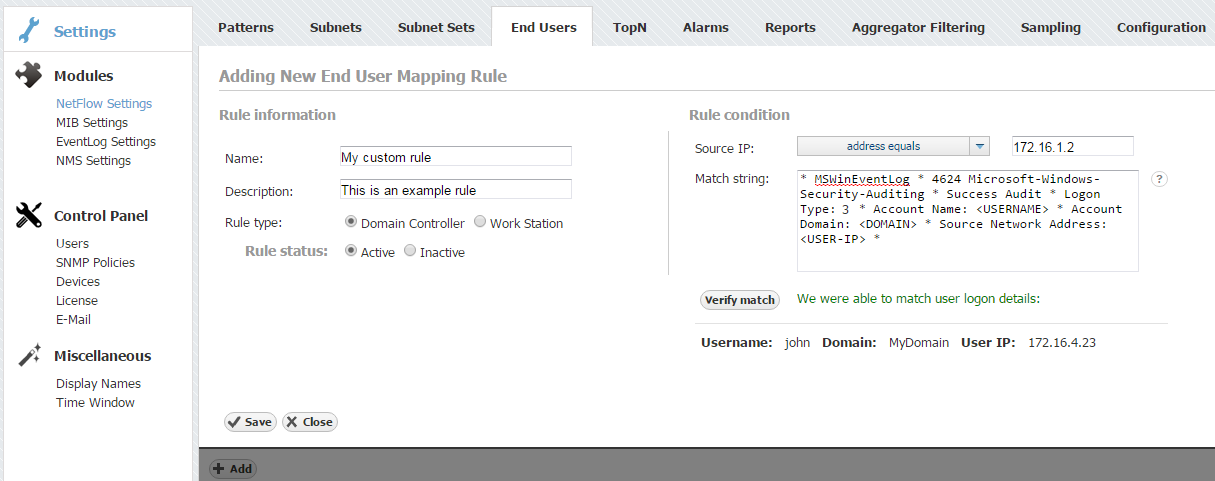
Step 2. Setup rule:
In upper right corner of Netvizura application navigate to ![]() > Settings > NetFlow Settings > End Users:
> Settings > NetFlow Settings > End Users:
- Click on + Add button
- Enter your own Rule Name and Description
- Set Rule type (in this example set Domain Controller)
- Set Rule status (in this example set Active)
- Enter Source IP (IP address of Domain Controller)
- Copy and paste Match string from text editor into the Match string area
- Click on Verify match button
- Click on Save button to save your rule (if verification is successful)
To check results of your work, navigate to NetFlow > End Users. If the three is empty, refresh your web browser with ctrl+F5.
In order to improve system performance, we recommend to set status as inactive for all rules that are not in use.
Specifying too broad subnet in the Source IP field might result in performance penalty. For best results consider changing Source IP to more specific value or concrete IP address.
Use help button: Move your cursor under the question mark on the screen for additional help.
You can easily verify the rule by clicking Verify. It will check if any Syslog message from the last 24 hours matches the rule.
- No labels